I really wanted to move away from Bad Behavior; there's only so much I'm interested in this topic. But the first two posts didn't cover everything I wanted to talk about so I wasn't left with that warm fuzzy feeling of completeness. If, like me, you're over the whole Bad Behavior series I'm really sorry.
This time I'm going to go over the last little tid-bits so you can protect your sites and make sure the "bad" people stay away. For the most part anyway.
White Listing
You can white list IP addresses and user-agents. IP addresses can be white listed using ranges (in the CIDR format) or single IP by editing the file 'whitelist.inc.php'. Open it up and edit the below:
// Includes four examples of whitelisting by IP address and netblock.
$bb2_whitelist_ip_ranges = array(
"64.191.203.34", // Digg whitelisted as of 2.0.12
"208.67.217.130", // Digg whitelisted as of 2.0.12
"10.0.0.0/8",
"172.16.0.0/12",
"192.168.0.0/16",
// "127.0.0.1",
);
User-agents can be white listed in the same file but require an exact match to what you add to the array.
$bb2_whitelist_user_agents = array(
// "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) It's me, let me in",
);
It's important to use white listing conservatively. Extremely so. You don't want to use white listing unless you positively, absolutely, have no other option.
Black Listing
There are two different ways to use black listing in Bad Behavior; manually adding entries to your black lists and using the http:BL feature.
To use Bad Behavior's http:BL features you must have an http:BL Access Key. It's a fairly simple process that requires registration with Project Honeypot. They'll give you a BL Access Key and you place it in the settings array of 'bad-behavior-generic.php'.
$bb2_settings_defaults = array(
'log_table' => 'bb_logs',
'display_stats' => true,
'strict' => true,
'verbose' => true,
'logging' => true,
'httpbl_key' => 'PLACE_YOUR_KEY_HERE',
'httpbl_threat' => '25',
'httpbl_maxage' => '30',
);
Once that's done your install of Bad Behavior will use your local black lists as well as the http:BL lists.
On the other hand, you may encounter some rare cases where your site is being spammed by a new agent. In this case you might want to manually add entries to your local black lists.
The black lists are placed within 'blacklist.inc.php'. It only accepts user-agents, probably because IP address blocking is essentially useless. You'll need to edit 3 different areas of the script:
The first is for strings that occur at the beginning of the user-agent.
$bb2_spambots_0 = array(
"
The next is for strings that occur anywhere within the user-agent string.
$bb2_spambots = array(
"\r", // A really dumb bot
"; Widows ", // misc comment/email spam
"a href=", // referrer spam
//etc...
And, best of all, there's also a regular expression (regex) array for the really difficult user-agents.
// These are regular expression matches.
$bb2_spambots_regex = array(
"/^{10}$/", // misc email spam
"/^Mozilla...$/i", // fake user agent/email spam
"/{8,}/",
// "/(;\){1,2}$/", // misc spammers/harvesters
// "/MSIE.*Windows XP/", // misc comment spam
);
It's also possible to add your own blacklists into your Bad Behavior install. This is pretty helpful if you have multiple installs and are sane enough to recognize the absurdity in maintaining multiple lists. Just build a blacklist service and add the info to 'blackhole.inc.php'.
Yeah, just build a blacklist server. Ummm... it's easy?
Customizing the Template
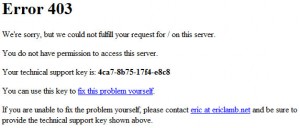
Every time a request gets blocked the system doesn't really know, 100%, that the request is bad; it just can't. So, instead of just dying, Bad Behavior displays a page with instructions on how to "unblock" yourself usually by just clicking on a link.
Unfortunately, the page looks like ass.
The idea, I'm sure, is that the page should have as small a footprint on the server as possible. One of the selling points is to lower bandwidth by blocking spam requests. No images, CSS or pretty allowed at all.
The flip side of this argument is that legitimate users who get this page will have an experience that's lacking in, ahem, quality.
You can change the look of the page by editing 'banned.inc.php'. It should be pretty self explanatory once you open the file what needs to be done.
If you want, you can also change the response messages. Those are stored in 'responses.inc.php'.
Well, that about does it; there's more to Bad Behavior but this series pretty well covered all the good parts.
This will be my last post on Bad Behavior; I swear.